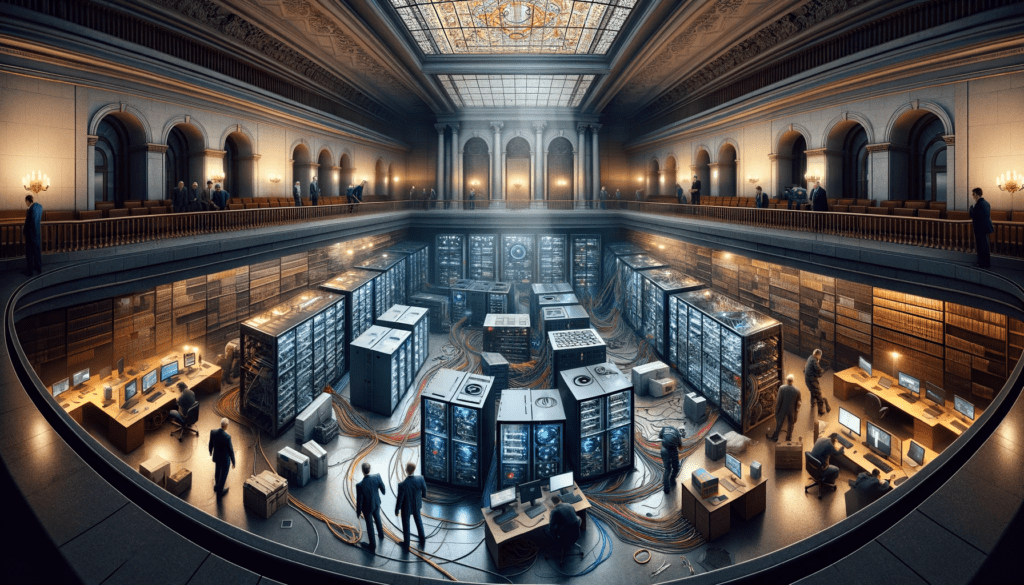
In a stunning development, a covert cryptomining operation was discovered under the floors of Poland’s Supreme Administrative Court in Warsaw. This revelation, initially reported by TVN24, highlighted a sophisticated operation that secretly utilized the court’s electricity. The maintenance worker who stumbled upon this setup in late August triggered a thorough investigation, unveiling the rig’s energy-intensive computers hidden in ventilation ducts.
Financial Implications: The Cost of Stolen Energy
The cryptomining rig, cleverly concealed, was allegedly pilfering thousands of Polish Zlotys in electricity each month, a significant expense considering the energy demands of such operations. Law enforcement’s involvement has now shifted to assessing the financial damage, engaging IT experts to determine the exact energy consumption and its cost.
Sophistication and Stealth: Evading Detection
Remarkably, the cryptomining computers were not connected to the court’s network but operated through independent modems. This strategy allowed the operation to remain undetected, circumventing traditional network monitoring and showcasing a sophisticated level of planning and execution.
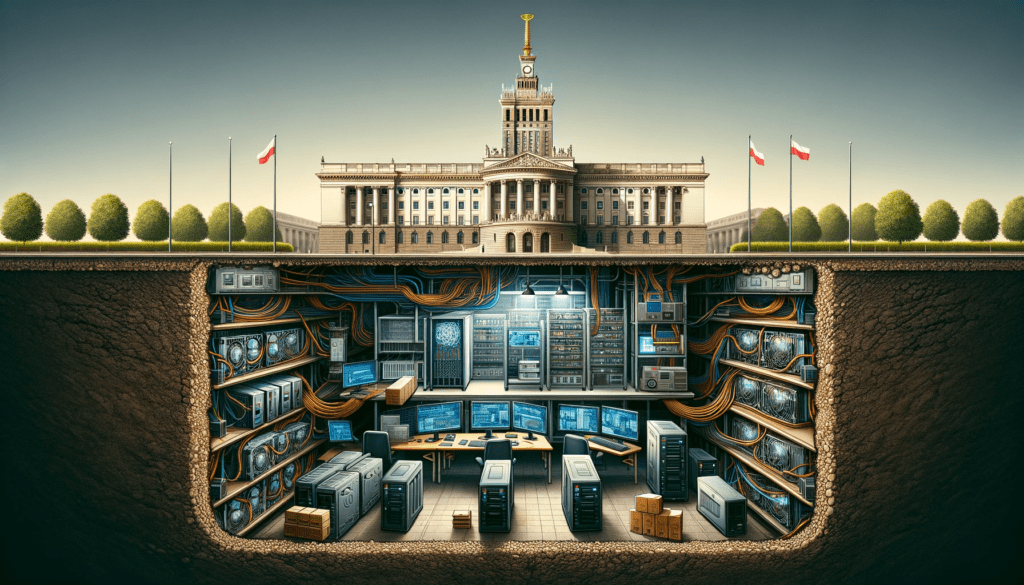
Broader Implications and Security Concerns
This incident isn’t an isolated case. Similar instances of crypto energy theft have been reported globally, including previous occurrences in Poland. The discovery raises crucial questions about the adequacy of current security measures in institutional settings and the challenges posed by emerging technologies like cryptocurrency mining.
Implications for Institutional Security
The cryptomining rig’s discovery beneath a key legal institution in Poland is a significant concern. It underscores the evolving tactics of crypto criminals and highlights the pressing need for enhanced cybersecurity measures in institutional frameworks. The incident serves as a stark reminder of the potential risks and vulnerabilities associated with advanced technological exploitation.
Collaborative Efforts and Future Preventive Measures
The joint efforts of law enforcement and IT professionals in dismantling the rig and assessing the damage reflect the importance of a multidisciplinary approach to combat such cyber threats. This incident acts as a call to action for institutions worldwide to reevaluate their security protocols and implement robust measures against similar covert operations.
A Cautionary Tale of Technological Exploitation
In conclusion, the discovery of this massive, covert cryptomining operation beneath a Polish court represents a complex blend of technological ingenuity and illicit exploitation. It serves as a cautionary tale, highlighting the evolving tactics of cyber criminals and the imperative for institutions to proactively upgrade their cybersecurity defenses in response to these sophisticated threats.